Cybersecurity Awareness Month - October 2024
It's a collective responsibility to Secure Our World.
Hello NEIU, it's the month of the year to celebrate Cybersecurity Awareness.
This year’s theme is Secure Our World. The theme recognizes the importance of taking daily steps to reduce data breach risks. It reminds us that securing the data we use at home, work, or wherever we go can help Secure Our World and reduce the likelihood of a successful cyber attack. This is a collective responsibility that takes simple steps and a commitment to maintain good security practices.
Intro
Cyber threats are real and can significantly impact those who have been victims. Cybercriminals continue to invent new and more tactical ways to lure their targets to click a link or download an attachment that is malicious to gain unauthorized access to computer systems and data or impersonate someone for financial gain. This year's theme reminds us of simple and practical ways to protect ourselves, our families, and our businesses from cyber threats and focuses on four key ways to do so when online. Each week will focus on a topic and will feature movie clips, training videos, posters, and online games.
- Week 1: Use strong passwords and a password manager
- Week 2: Turn on multi-factor authentication
- Week 3: Recognize and report phishing
- Week 4: Keep software updated
In addition to the four topics, we will include other good practices to maintain when on or offline.
Events
Recorded virtual sessions
- Watch and learn about Cybersecurity Career Paths by the National Initiative for Cybersecurity Careers and Studies (NICCS).
Live sessions hosted by the Computer Science Department
*Attendees will have the opportunity to win $25 Amazon gift cards.
- "From Heuristics to AI-Powered Security: A Case Study with Designing of Effective Honeypot Systems" by Dr. Sencun Zhu. Thursday, Oct. 24 from 9:30-10:45 a.m. on the Main Campus in Alumni Hall. See Dr. Zhu's bio.
- "AI Security and Threat Models" presented by Dr. Mohamed Abuhamad, Loyola University, Chicago. Thursday, Oct. 24 from 5:30-6:50 p.m. on the Main Campus in Alumni Hall. See Dr. Abuhamad's bio.
Other resources from the Computer Science Department
- The Computer Science Department has provided additional resources for Cybersecurity Awareness Month. To learn more, please visit the Computer Science Department.
- Cybersecurity career paths (NEIU degree programs and certifications in cybersecurity).
Thanks, and have a cyber-safe October!
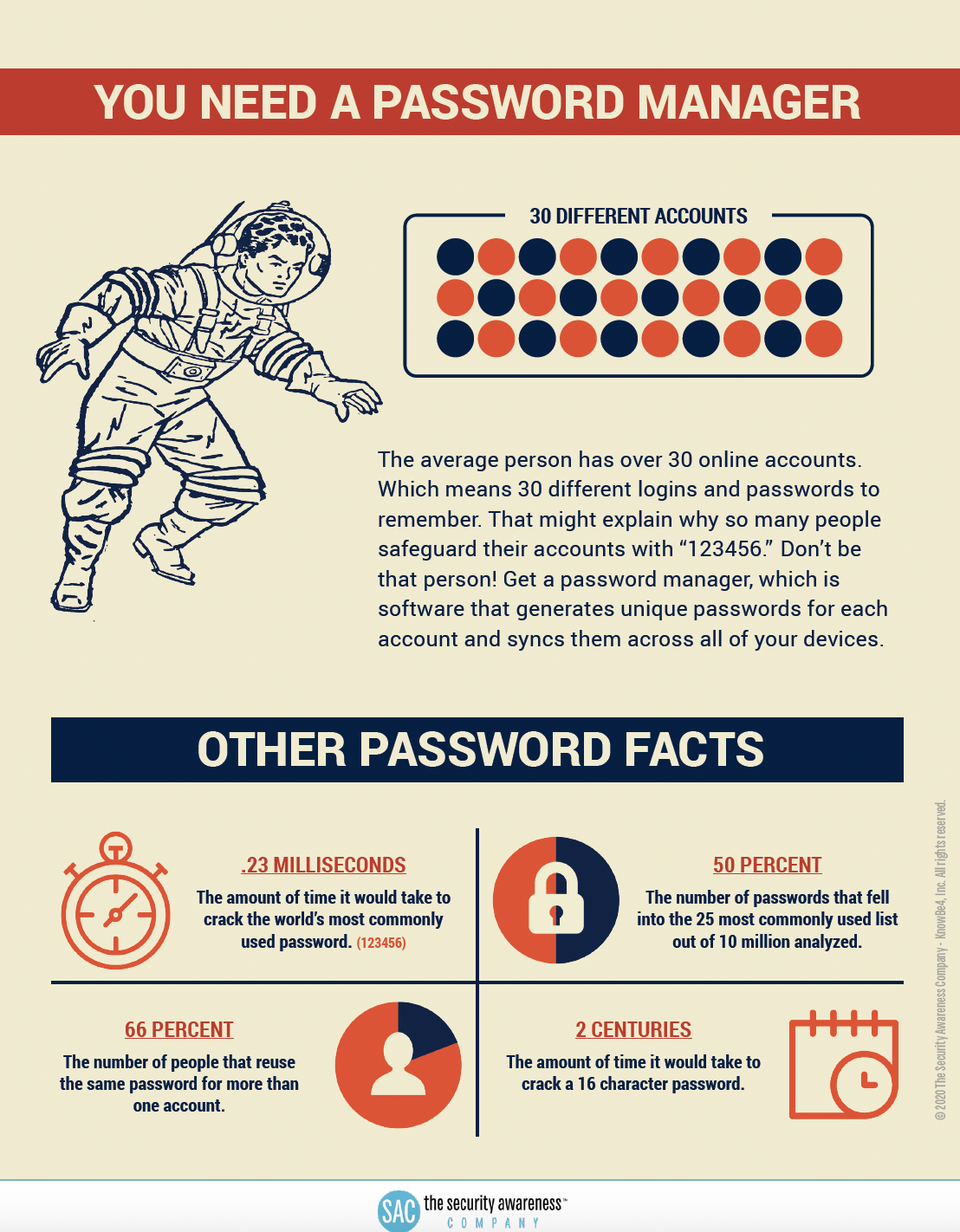
Week One: Use Strong Passwords and a Password Manager
"There are many ways to keep a user account secure, using a strong password is the first basic step" (University Technology Services).
Statistics:
- 35% of respondents said weak passwords were the main reason their accounts were hacked. (Forbes)
- 86% of breaches involve stolen credentials, according to Google Cloud's 2023 Threat Horizons Report.
- 30% of respondents believed their accounts were compromised because they used the same password across multiple platforms. (Forbes)
- 50% of respondents said that account security was the top reason for using password managers. (Bitwarden)
focus
This Week's Focus: Strong Passwords and Password Managers
Using simple passwords like birthdays, holiday seasons, weather, sports teams, anniversaries, hobbies, etc., can be convenient and easy to remember however they also make it very easy and convenient for hackers to crack. According to the National Cybersecurity Alliance, "Using weak passwords is like locking the door but leaving the key in the lock."
With the use of artificial intelligence to carry out cyber crimes, cracking passwords has never been easier but a long and unique password makes a hacker's job more difficult even with the best tools.
Remembering all unique passwords for various accounts has its challenges, but with password managers, users can easily and quickly create unique passwords or passphrases, do not need to remember all their passwords, can seamlessly and securely access accounts on multiple websites and devices, and protect against password reuse and compromise.
You only need to remember the password to your password manager account. This password or passphrase should be at least 16 characters long and unique.
My role: I am the first line of defense to the system and data I use. The stronger my password or passphrase, the safer my and my organization's data is. Remember, we can Secure Our World when we embrace a good security culture.
Training videos and movie clips (Log into KnowBe4 and select the Library tab). Enjoy watching!
The materials below provide examples and practical ways to secure your user account:
- Restricted Intelligence Season 1: Ep 01 - The Test (Passwords and Access) (4 minutes).
- How to Use a Password Manager (5 minutes).
- Confessions of a Password Protector (4 minutes).
Game: Cybersecurity Trivia Twirl (external link).
Posters: Click on each one to learn more.
Please see the University's Password Management Policy (recently updated).
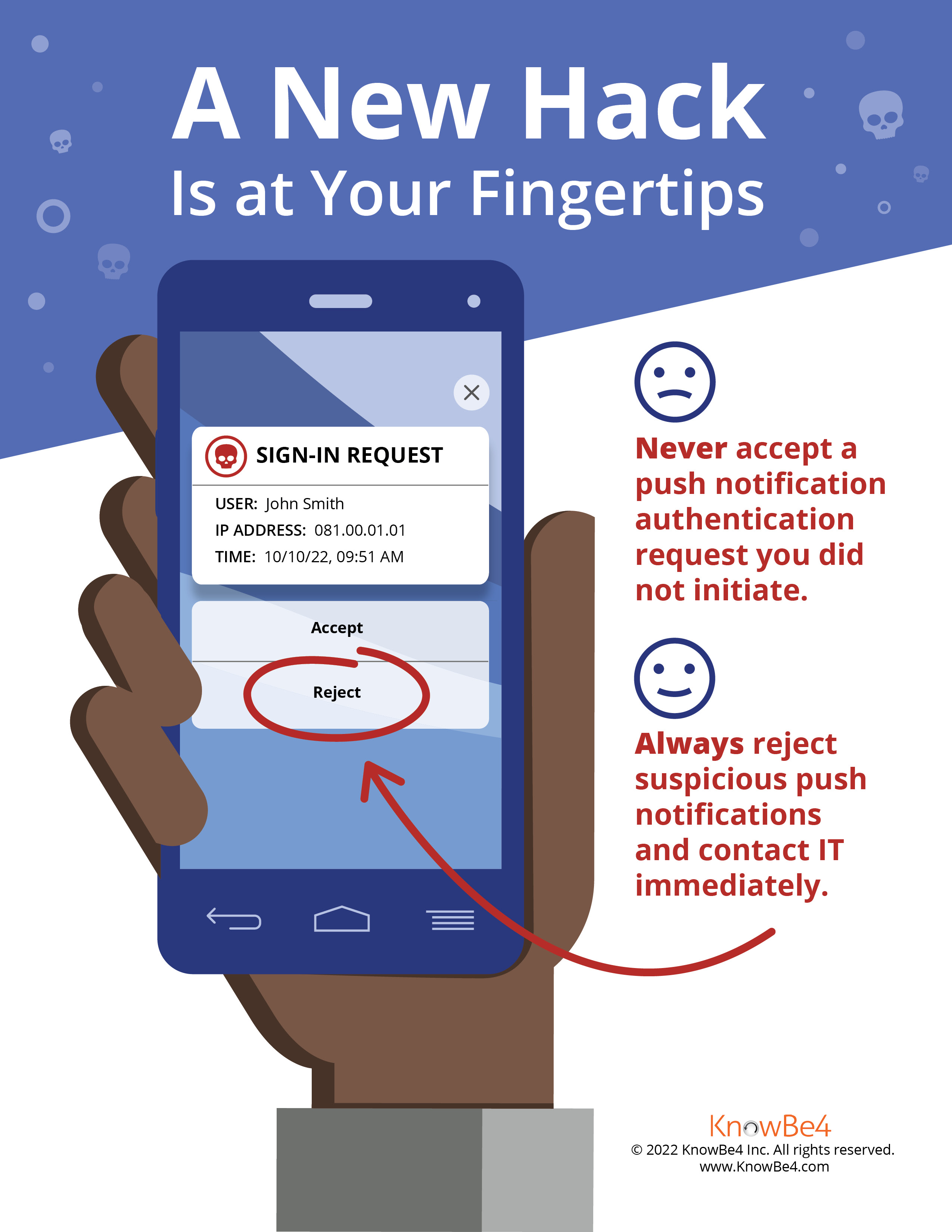
Week Two: Turn on Multi-Factor (MFA) Authentication
"Using multi-factor authentication is like having someone look out for you" (University Technology Services).
Statistics:
- Around one in four companies have turned to MFA after a cybersecurity breach. (DUO)
- Using MFA on an account makes it 99% less likely to be hacked. (Cybersecurity & Infrastructure Security Agency - CISA)
- 99.9% of hacked accounts did not use MFA. (Microsoft)
focus
This Week's Focus: Turn on Multi-factor Authentication (MFA)
The use of multi-factor authentication (MFA) also called 2FA has nearly doubled since 2020 according to Okta, and the primary reason is that MFA is considered one of the strongest authentication methods. Some surveys report that users see MFA as an additional step that could sometimes be cumbersome, but over time, users have found that MFA lends itself to securing their user accounts where their passwords have been compromised.
MFA is a tool that requires an additional step in the user authentication process when logging into an account. It is designed to ensure that a user has all the verification information (such as a username, password, and MFA information) before authenticating the user and granting access to the relevant resources. MFA provides an additional layer of security for user accounts.
There are different MFA methods including:
- MFA push notifications are sent to an MFA mobile app which the user can approve or decline.
- Randomly generated codes are presented on an MFA mobile app or MFA hardware device, or MFA codes are sent via a call, text, or email.
- A PIN (personal identifiable number) is assigned to a user which they must provide during authentication.
- Fingerprint, palm scan, face ID, or voice recognition.
- Security questions that users must answer.
Almost all organizations that provide financial, health, tax, or benefits services or other services that handle personal information require their employees to use MFA and provide MFA to their customers.
My role: I can safeguard access to my data and my organization's information by using all the resources available to help me do so.
Remember, you can Secure Our World when you take responsibility for information security. Below are some simple but practical steps that can help you keep your user account secure:
- Don't delay using MFA if it is available. Learn more about the University's MFA tool.
- Most MFA still require passwords or passphrases. Use strong passwords and don't share them. The longer your password, the more difficult it is for hackers to crack.
- Keep your devices locked when not in use and store them away in your absence. MFA will not protect your user account or information if you leave your computer unlocked and unattended.
- Watch out for phishing attacks. Stop, look, and think before you respond to unsolicited or suspicious emails, texts, or calls.
- Watch out for MFA hacking. Don't approve any MFA push notification that you did not request or share your MFA code with anyone.
- Visit the Cyber Smart Tips page for more good practices.
Training videos (Log into KnowBe4 and select the Library tab)
The materials below provide examples and practical ways to secure your user account:
- Multi-factor Authentication: First Steps (2 minutes).
- Multi-factor Authentication Attack (5 minutes).
- MFA Fatigue (3 minutes). An external awareness video by Arctic Wolf.
- Protect Our World with MFA (2 minutes). An external awareness video by CISA.
Posters: Click on each one to learn more.
Week Three: Recognize and Report Phishing
"When you report, we get stronger" (KnowBe4).
Statistics:
- Phishing attacks account for more than 80% of reported security incidents. (CSO Oline)
- 57% of organizations see weekly or daily phishing attempts. (GreatHorn)
- 68% of breaches involved a human element in 2024. (Verizon)
- In 2023, the average cost of a data breach caused by phishing was $4.72 million. (Upguard)
focus
This Week's Focus: Recognize and Report Phishing
What is Phishing?
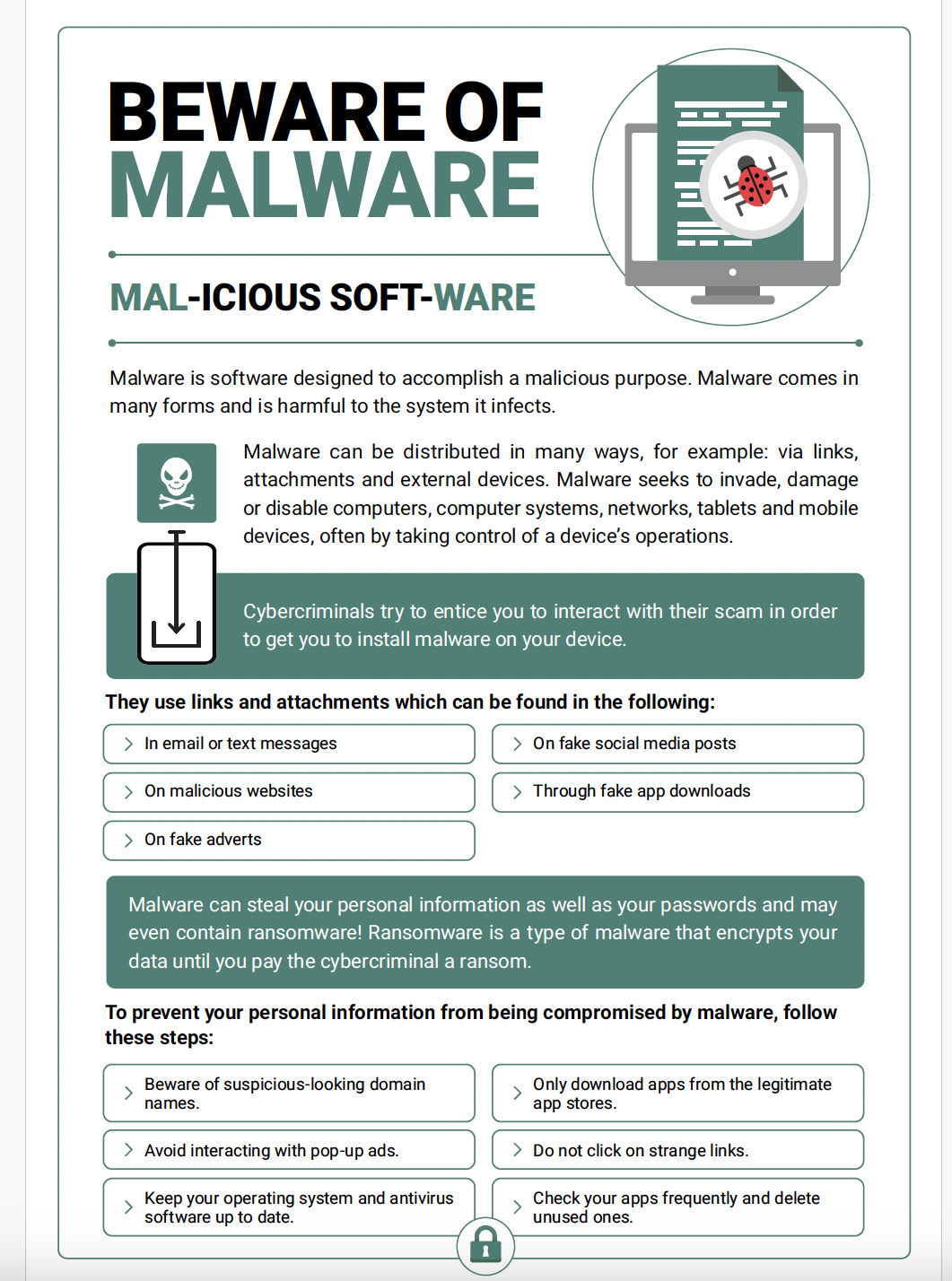
Phishing is simply a tactic cybercriminals use to make their target believe a lie and act on that lie for the gain of the cybercriminals. Phishing is usually carried out using different methods including emails, text messages, social media, mobile apps, phone calls, and even QR codes. With the use of Artificial Intelligence, some phishing scams involve impersonating people making them so real that the target could easily fall for them if not cautious.
Phishing has been reported as one of the most common and successful cybersecurity attack methods and accounts for the highest cause of security incidents. This is because it does not often require a system flaw, failure, or a technical tool but plays on human trust and reasoning to succeed. According to KnowBe4, "The problem isn't the lack of software designed to detect, prevent, and protect – it's that human response is a required part of every phishing attack that users seem to be happy to oblige."
We must therefore know how to recognize phishing so we don't fall for it!
My role: Be aware of the different phishing tactics, and learn how to respond to and report them. A good way to prevent being phished is to stop, look, and think before you respond.
Recognizing and responding to phishing:
- Who is the message coming from and can the sender be trusted? Look for misspellings or unusual texts or characters in the email address, message, or the link provided. Watch out for unfamiliar email addresses or telephone numbers.
- Does it appear to be a random or unusual message even if the person or entity is known? Contact the person or entity directly using known contact information such as their telephone number or visit the organization's website.
- Is the message alarming and are you being asked to take urgent action like verifying a financial transaction, confirming a password change, downloading an attachment, or purchasing items on the sender's behalf? Check first with the helpdesk or information security team for advice.
- Are you being asked for a favor because the sender or caller appears "in need"? Don't take any action that could compromise your or other people's information or send money to the sender. Verify the person first before you respond.
- Are you being offered a service and asked or directed to provide information that may be sensitive such as your login details, MFA approval or code, social security number, DOB, address, etc? End the communication and contact the relevant organization from a known number.
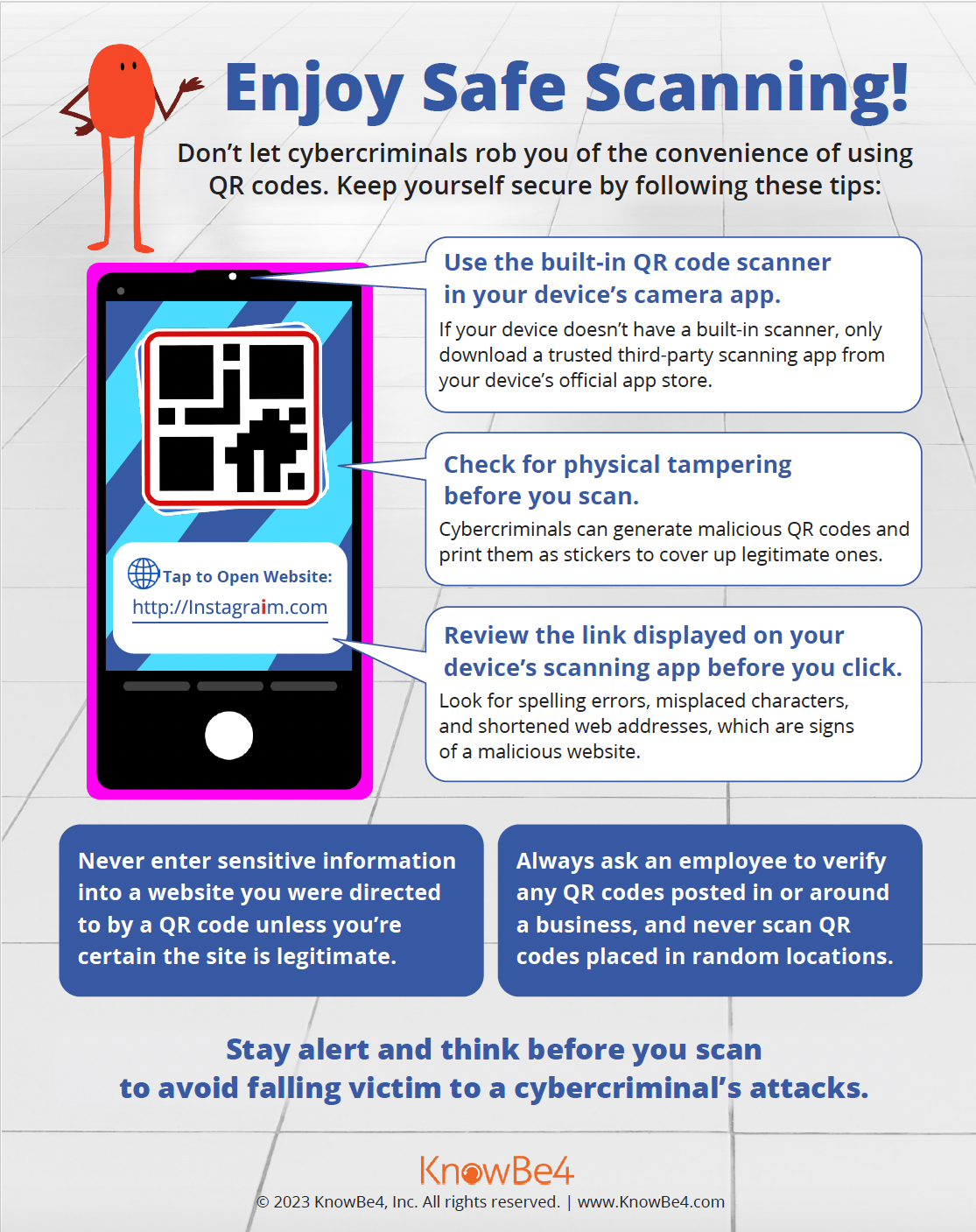
- Are you being asked to scan a QR code from an unknown or unfamiliar source? Don't scan if you don't know. Just scanning a QR code could download malware on your device. Use your device camera to preview the URL before clicking.
- Verify applications before downloading them and download only from trusted sources. Use the verify app feature in your mobile device app store to detect and protect your device from harmful apps.
- Watch out for freebies. If it is too good to be true, it probably is!
Reporting phishing:
You should report phishing as soon as possible to stop it from spreading further. Also, you should mark the email as spam to stop receiving emails from the sender. Different email platforms such as Outlook, Yahoo, Gmail, etc., have features for blocking and reporting phishing, and you should check each platform on how to do so. In Nmail, follow the steps below:
-
Select the three vertical dots in the phishing or spam email as shown in the image below:

- Select either block (sender's name), report spam, or report phishing from the options.
You should also forward the email to abuse@neiu.edu so the helpdesk can act on it.
Training videos and movie clips (Log into KnowBe4 and select the Library tab to see or search for the videos). Enjoy watching!
The materials below provide examples and practical ways of combating phishing:
- The Inside Man: Season 1 Ep 03 - On Our Side (Phishing Attacks) (7 minutes).
- QR Codes: Safe Scanning (4 minutes).
- Criminal Minds: Mobile Applications (4 minutes).
- Security Snapshots - "A Big Deal" (Reporting incidents) (2 minutes).
Game: Spot the Phish Game: Bad Links
Posters: Click on each one to learn more.
Week Four: Keep Software Updated
“When notified about software updates, especially critical updates, install them as soon as possible. Cybercriminals won’t wait so we shouldn’t either!" (CISA).
Statistics:
- The National Vulnerability Database (NVD) recorded 28,831 vulnerabilities in 2023, up from 25,081 in 2022.
- In 2023, 25% of security vulnerabilities were immediately targeted for exploitation, with the exploit published on the same day as the vulnerability itself. (Qualys)
- 48% of all universities and 70% of the top 500 have software products with known exploited vulnerabilities. (UpGuard)
- In 2023, 40% of ransomware attacks in higher education were due to exploited vulnerabilities. (EdTech)
Focus
This Week's Focus: Keep Software Updated
Software is the heart of every computer and IT service we use. Imagine a world without software for work, learning, carrying out daily tasks, or connecting with people… Imagine a world without mobile apps or online services…
As software is an essential commodity in today’s world, hackers always look for ways to exploit vulnerabilities (weaknesses) in software. The easiest way to do this is to look for software not updated with the relevant security patches. This means that every time a software update is delayed or ignored, it creates an opportunity for a hacker to compromise the computer running that software. If we maintain the latest updates and fixes for the software we use, we benefit from using the latest features the software offers and make our devices and information more secure.
My role: I will use and manage software responsibly to keep hackers out of my business.
Remember, you can Secure Our World when you take responsibility for the appropriate use and handling of software. Below are some practical steps for keeping software updated and staying protected from malicious software:
- Enable automatic software updates on your devices. This makes it easier to keep your devices running secure software.
- If available, set up notifications for new updates from the software vendor or your organization. Delays will leave your devices open to malware.
- Only download software directly from verified sources and app stores.
- There are many apps designed to compromise your device and steal your data. Don't fall for app freebies!
- Watch out for fake software fixes. If you receive an unusual email, text, call, or a pop-up window to fix your device or update your software, contact IT first to check before downloading the software.
Training videos and movie clips (Log into KnowBe4 and select the Library tab to see or search for the videos). Enjoy watching!
The materials below provide examples and practical ways to secure your user account:
- Restricted Intelligence Season 7: Ep 04 - Bear The Consequences (Software Updates) (4 minutes).
- Protecting Your Devices (5 minutes).
Posters: Click on each one to learn more.
Live sessions hosted by University Technology Services and Computer Science Department
*Attendees will have the opportunity to win $25 Amazon gift cards.
- "From Heuristics to AI-Powered Security: A Case Study with Designing of Effective Honeypot Systems" by Dr. Sencun Zhu. Thursday, Oct. 24 from 9:30-10:45 a.m. on the Main Campus in Alumni Hall. See Dr. Zhu's bio.
- "AI Security and Threat Models" presented by Dr. Mohamed Abuhamad, Loyola University, Chicago. Thursday, Oct. 24 from 5:30-6:50 p.m. on the Main Campus in Alumni Hall. See Dr. Abuhamad's bio.
Thank you for participating in this year's Cybersecurity Awareness Month.